Introduction
In recent years, stories of “fake” base stations capable of tracking users and collecting their personal data without users’ knowledge have emerged. The current way of protecting privacy does not provide any protection against an active attacker on the air interface, claiming to be a legal network that has lost its temporary identity.
One confidentiality issue present in all prior mobile network incarnations is that the mobile device has to reveal its International Mobile Subscriber Identity (IMSI) to the network. Once the subscriber is authenticated and encryption is activated an anonymized temporary identifier would then be assigned and used. Unfortunately, this early moment of openness can be used to make the UE reveal its subscriber identity by malicious actors at any time, e.g. with fake base stations telling the UE that the temporary identifier is unknown.
An active man-in-the-middle adversary can intentionally simulate this scenario to force an unsuspecting user to reveal its long-term identity. These attacks are known as “IMSI catching” attacks and persist in today’s mobile networks including the 4G LTE/LTE-Adv.
IMSI-catcher Issue
IMSI catching is an attack aiming to reveal the identity of a user by catching the IMSI of the user’s UE. The IMSI-catcher requests the long-term subscriber identity from a mobile device. Since this is a valid request in normal operations, the mobile device replies with its IMSI according to standard protocols. The IMSI-catchers can be used, for example, to monitor who is moving in a certain area, or to track which locations a given subscriber is visiting. In addition, more advanced IMSI-catchers can spy on the traffic to and from the mobile device. Current mobile broadband standards do not address threats from IMSI-catchers. This problem is non-minor since the IMSI requests may occur when there is no security context available to cryptographically protect the request.
A current solution for protecting subscribers’ identity is based on a serving network assigning a randomly generated Temporary Mobile Subscriber Identity (TMSI) to the mobile device at regular intervals. The long-term IMSI is used only as a fault recovery mechanism and when a TMSI has not yet been assigned. The recovery mechanism is needed to avoid lock-out of a mobile device when errors occur, e.g., when the serving network or the mobile device has lost the TMSI.
The mobile device falls back to using the IMSI whenever the serving network requests. This recovery mechanism is what IMSI-catchers exploit to obtain the IMSI from mobile devices.
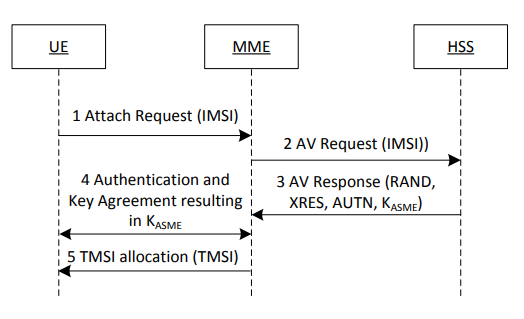
AKA Procedure in LTE
Hence, the current way of protecting privacy does not provide any protection against an active attacker on the air interface, claiming to be a legitimate network that has lost the temporary identity. Neither is there any protection against passive eavesdroppers who are present when IMSI requests are made.
Subscription Unique Permanent Identifier (SUPI)
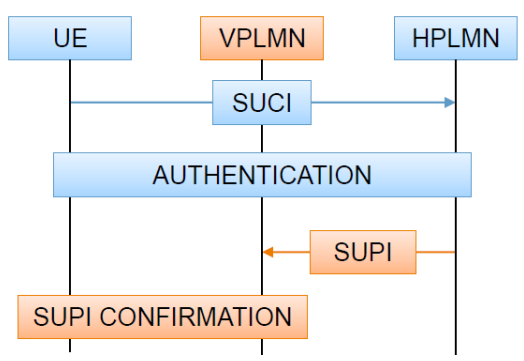
All subscribers within the 5G Core are allocated a globally unique 5G subscription permanent identifier (SUPI). The SUPI is in the form of the traditional international mobile subscriber identity (IMSI) or network access identifier (NAI). The service provider allocates this to each SIM card that is inserted into the UE. SUPI is never sent in clear text across the RAN because if it is intercepted by rogue elements, the UE can be spoofed and can also result in DoS attacks.
Rather the UE is assigned a globally unique temporary identifier (GUTI), which is used to identify the UE over the radio link. Utilizing the IMSI ensures various roaming and interworking scenarios are supported. This SUPI value in 5G can be the IMSI value, as used in previous generations, or it can be the NAI for non-SIM devices.
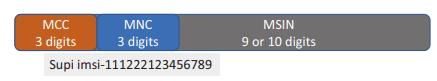
The SUPI normally consists of 15 or 16 decimal digits, which comprises the MCC-MNC-MSIN.
Subscription Unique Permanent Identifier (SUPI)
The SUPI Components:
- MNC and MCC are the mobile network and country code used to identify the country and the specific service provider. A combination of the two can identify a mobile network uniquely across the globe.
- MSIN is the abbreviation for a mobile subscription identification number. It consists of 10 digits and is sed to identify a mobile phone subscriber by the service provider.
Subscription Concealed Identifier (SUCI)
For privacy reasons, the SUPI from the 5G devices should not be transferred in clear text and is instead concealed inside the privacy-preserving SUCI. Consequently, the SUPI is privacy protected over the air of the 5G radio network by using the SUCI. For SUCIs containing IMSI-based SUPI, the UE, in essence, conceals the MSIN (Mobile Subscriber Identification Number) part of the IMSI. On the 5G operator-side, the SIDF (Subscription Identifier De-concealing Function) of the UDM (Unified Data Management) is responsible for de-concealment of the SUCI and resolves the SUPI from the SUCI based on the protection scheme used to generate the SUCI.
SUPI and SUCI in 5G
The SUCI protection scheme used in this data set is ECIES Profile A. The size of the scheme-output is a total of the 256-bit public key, 64-bit MAC & 40-bit encrypted MSIN. The SUCI scheme-input MSIN is coded as hexadecimal digits using packed BCD coding where the order of digits within an octet is the same as the order of MSIN. As the MSINs are odd numbers, bits 5 to 8 of the final octet are coded as ‘1111’.
In order to fight against IMSI catchers, 5G introduces the Subscriber Permanent Identifier (SUPI), as replacement of the IMSI, and a PKI for the encryption of the SUPI into the Subscriber Concealed Identifier (SUCI).
5G improvements in Subscribers Privacy
5G improves confidentiality and integrity of user and device data. It protects the confidentiality of the initial non-access stratum (NAS) messages between the device and the network. As a result, it is no longer possible to trace user equipment (UE) using current attack methodologies over the radio interface; protecting against man in the middle (MITM) and fake base station (Stingray/IMSI catcher) attacks.
Also, It supports the below:
- Encryption of SUPI with the public key of the home operator (SUCI).
- Routing information (home network ID) is clear.
- SUPI revealed to VPLMN only after authentication.
- Binding of SUPI into the key.
- UE and HPLMN have to use the same SUPI: requested for lawful intercept purposes.
- Respond to identifier requests with SUCI.
- No SUPI based paging.
Conclusion
In previous network generations (2G, 3G, 4G), the identifier of the subscriber, aka IMSI, is transmitted in clear text over the air interface and hence is subject to certain threats. So-called IMSI catchers can be obtained easily at a relatively low cost and are used by attackers to get hold of the IMSI and consequently retrieve valuable and highly private information such as the location of the subscriber, the SMS sent or even data being transferred.
In 5G, this security weakness is addressed. The 5G successor of the IMSI, the Subscriber Permanent Identifier (SUPI), can be encrypted and transmitted over air as a Subscriber Concealed Identifier (SUCI). The key used to encrypt the SUPI is securely stored within the 5G SIM / eSIM. According to the 3GPP specifications, the encryption procedure as such can either be performed within the device or within the 5G SIM / eSIM.