Introduction
The rise of the Industrial Internet of Things (IIoT) heralds a transformative era in the world of industry, bringing forth an interconnected web of devices, systems, and platforms that can seamlessly exchange data and insights in real-time.
At the heart of this revolution lies communication protocols. These are the channels that allow IIoT devices to talk, understand, and respond to each other.
Among the diverse array of communication protocols vying for dominance in the IIoT sphere, random access protocols stand out for their distinct potential. These protocols, traditionally associated with telecommunication networks, present an alternative communication method, eschewing the established norms and promising greater efficiency and reduced latency for sporadic IIoT users.
Historical Overview of Random Access Protocols
Random access protocols have an illustrious history that dates back several decades, deeply intertwined with the evolution of communication technologies. Let’s journey through the annals of time to understand the roots and progression of these protocols.
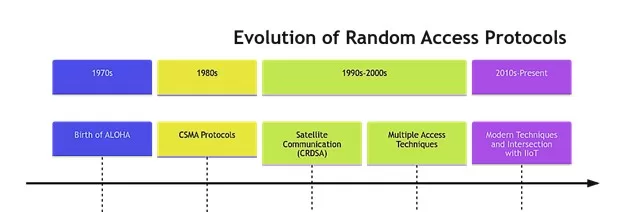
Figure 1: Evolution of Random Access Protocols
Birth of ALOHA and Packet Broadcasting
The genesis of random access protocols can be traced back to the early 1970s with the development of the ALOHA system by the University of Hawaii. The objective was simple yet revolutionary: establish a computer communication system across the Hawaiian Islands using UHF radios. The initial ALOHA system used a two-step process where users would send data whenever they wanted and then listen for a confirmation. If the confirmation wasn’t received, the data would be retransmitted. This rudimentary approach was the first instance of a pure ALOHA, which later evolved into slotted ALOHA to improve efficiency by dividing time into discrete slots.
Collision and the Emergence of Carrier Sense Protocols
The ALOHA system’s success and its challenges with data collisions led to the development of Carrier Sense Multiple Access (CSMA) protocols. These protocols made devices ‘listen’ to the network before transmitting. If the channel seemed busy, the device would wait, thus reducing the chances of collision. CSMA’s variations, like CSMA/CD (Collision Detection) and CSMA/CA (Collision Avoidance), further refined this process.
Broadening Horizons: Satellite and Beyond
As technology advanced, the application of random access protocols wasn’t limited to terrestrial networks. The satellite communication domain, with its unique challenges of long propagation delays and high setup costs, found solace in random access techniques. Variants like Contention Resolution Diversity Slotted ALOHA (CRDSA) emerged, offering enhanced solutions for satellite packet networks.
Multiple Access Protocols
With the proliferation of users and devices, especially in urban environments, the need for more sophisticated random access protocols became evident. This era saw the rise of non-orthogonal multiple access (NOMA) techniques, allowing multiple users to transmit simultaneously over the same frequency bands.
Adapting to Modern Needs: The Intersection with IIoT
The IIoT realm, characterized by sporadic transmissions and the need for ultra-reliable low-latency communication, posed a fresh set of challenges. Traditional grant-based access mechanisms, while efficient for continuous data streams, were ill-suited for IIoT’s sporadic nature. Here, random access protocols, with their inherent flexibility and reduced signaling overhead, found a new playground.
Random Access Protocols in IIoT
The Industrial Internet of Things (IIoT) has paved the way for a revolutionary transformation in various industries, from manufacturing to transportation and beyond. We mainly have two ways to manage how devices get access to radio signals: scheduled access and random access.
With scheduled access, a central control point, called the Base Station (BS), gives specific time slots or frequencies to each device, known as User Equipment (UE). This can be fixed, like in the Time Division systems, or it can change based on needs, like we see in LTE or NR systems.
On the other hand, random access is a bit more flexible. Here, the BS sends out a general message about which signals are free. Then, it’s up to the devices (UEs) to choose one based on certain rules and chances. But there’s a catch: since many devices might pick the same signal at the same time, they can interfere with each other. This is a risk, especially for Industrial IoT (IIoT) where reliability is key.
So, how do we decide which method to use? It really depends on what the system needs, how often data is sent, and where it’s being used. Scheduled access is good because it avoids devices overlapping, but it has a downside: it needs a lot of back-and-forth messages to set things up, which can slow things down. This isn’t great for IIoT systems that send data only once in a while. Random access, on the other hand, is quicker to set up, but there’s always a bit of uncertainty because of the chance of interference.
Establishing Random Access Connection
Modern tech solutions often mix two methods for connection: random and scheduled access techniques. While systems like LTE and 5G NR are centered on using permits, they depend on random access during the initial connection phase. This is because it’s unpredictable when a device, or UE, will request a link. This initiation, termed the RA action, starts when a UE shifts from a dormant mode (like RRC-IDLE or its equivalent in NR) to a connected mode. This shift might occur when a device first signs into the network, after staying idle, or if there’s a connection drop.
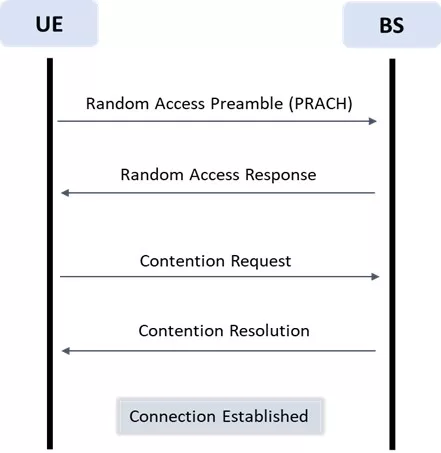
Figure 2: Connection Establishment in Random Access
The above diagram offers a streamlined visualization of this intricate process. Initiated by the UE, the sequence begins with a connection request, followed by an acknowledgment or challenge from the BS. The UE then responds, leading to the BS confirming the successful establishment of the connection. This back-and-forth interaction ensures that both entities are synchronized, paving the way for seamless communication. Such procedures are quintessential, especially considering the sporadic nature of IIoT traffic patterns and the need for prompt device-to-network integrations.
Studies focusing on the RA mechanisms of LTE and NR systems, especially with the rise of numerous IoT devices, have been extensive. Innovations have been proposed to enhance preamble distribution, adjust guidelines, and refine the system for smoother operations. As many IIoT devices send information sporadically, they frequently initiate the RA action. This consistent initiation might cause delays and potentially disrupt services during heavy traffic. Therefore, it’s vital to consider these RA sequences when evaluating the efficiency and dependability of systems like NR.
One of the defining characteristics of the IIoT revolution is the sheer number of connected devices. Traditional communication systems might find it challenging to scale to this magnitude. However, random access protocols, especially with the integration of application awareness and cross-layer design, are well poised to handle the scalability demands of the IIoT landscape.
Collision Channel and Performance Modeling
The essence of random access protocols hinges on their interaction with the communication medium, particularly how they deal with the ubiquitous challenge of collisions. As the digital realm evolved, so did the sophistication in modeling these channels and assessing performance.
Collision Channel Model:
Traditionally, random access protocols were scrutinized under the lens of the collision channel model. Simpler and less intricate than its information-theoretic counterparts, like the Gaussian Multiple Access Channel (MAC), the collision channel model provided a foundation for analyzing the expected behavior of these protocols. Its reduced complexity makes it amenable for real-time analysis, particularly in scenarios demanding swift resource allocation and overload control.
While the collision channel model stands out for its abstract simplicity, it does come with its caveats. In high-reliability scenarios, especially as seen in Industrial Internet of Things (IIoT) applications, not only the expected but also the outliers in the distribution matter. Thus, there’s a compelling need to model corner cases and higher-order effects for a holistic understanding.
SIC & MPR models:
Recent advancements in communication techniques like Successive Interference Cancellation (SIC) and Multi-Packet Reception (MPR) have challenged the traditional collision channel model’s predictions. They offer enhanced performance, often surpassing the benchmarks set by the conventional model.
K-MPR Channel Model:
Among the significant advances, the K-MPR channel model deserves special mention. While it brings a probabilistic version that lends more precision to modeling higher-order effects, it operates under the presumption that MPR capabilities are static and predetermined. However, in real-world scenarios, factors such as deployment, power control, channel coefficients, and even contention parameters make this assumption a hard sell. Hence, the quest for an adaptable model that can faithfully represent the high reliability demands of modern applications continues.
The discrepancies between existing models and the real-world challenges highlight the exigency for continued research. Efforts need to be directed towards creating models that seamlessly meld with varying scenarios, from static and predetermined environments to dynamically changing ones.
Challenges in Random Access Protocols for IIoT
As industries worldwide rush to integrate IIoT solutions, understanding these aspects becomes imperative for consistent growth and innovation.
- Complexity in Deployment Scenarios:
The heterogeneous nature of IIoT devices, combined with varied deployment scenarios, makes the universal application of a single protocol problematic. The dynamic environments in which these devices operate can often lead to unpredictable behavior, requiring flexible protocols that can adapt in real-time. - Diverse Traffic Patterns:
IIoT devices can generate a wide range of traffic patterns, from periodic updates to bursty, high-priority alerts. Accommodating these varying traffic needs without causing congestion or delay remains a significant challenge. - Energy Constraints:
Many IIoT devices are battery-powered, emphasizing the need for energy-efficient communication protocols. Ensuring long device lifetimes while maintaining robust communication can be a balancing act. - Scalability Issues:
The exponential growth in the number of connected devices can lead to scalability concerns. Ensuring that random access protocols can efficiently manage this massive device influx without sacrificing performance is a looming challenge. - Security Vulnerabilities:
With the increasing interconnectivity of IIoT devices, security becomes paramount. Ensuring that random access protocols are resistant to various cyber threats, from eavesdropping to denial-of-service attacks, is crucial.
Conclusion
The transformative potential of the Industrial Internet of Things (IIoT) is undeniable, with communication protocols serving as its backbone. As random access protocols emerge as a promising contender in this space, it’s evident that their adaptability and efficiency could redefine IIoT communications. However, the complexities of deployment, diverse traffic patterns, energy constraints, scalability, and security concerns pose significant challenges. As we delve deeper into the intricacies of these protocols, a pertinent question arises: How can we further optimize random access protocols to meet the evolving demands of IIoT, ensuring seamless integration and robust performance? This opens the door to exploring advanced models and techniques that can bridge the gap between theoretical predictions and real-world IIoT challenges.
References
- 3GPP (2019) TR 38.825 V16.0.0-Technical Specification Group Radio Access Network; Study on NR industrial Internet of Things (IoT); (Release 16) (2019)
- Cosmas Ifeanyi Nwakanma et al. “3GPP Release-16 for Industrial Internet of Things and Mission Critical Communications”, IEEE Xplore, 2020.
- Abramson.“The ALOHA System: another alternative for computer communications”. (AFIPS). ACM. 1970, pp.281–285.

