Introduction
The integration of 5G wireless technology into IIoT leads to a new era of industrial capability, distinguished by its high-speed data transmission, reduced latency, and enhanced reliability—key attributes to satisfy the rigorous demands of modern industrial applications.
Yet, as we embrace the seamless interplay between 5G and IIoT, the underpinning Time-Sensitive Networking (TSN) standards have become a critical component for achieving determinism within industrial communications. This precise timing and synchronization are vital for ensuring that complex, automated operations can occur without disruption, a hallmark of the efficiency gains promised by Industry 4.0.
However, the incorporation of 5G brings forth its own set of challenges, chiefly among them the development of a robust security framework.
Historically, IIoT applications have focused on the deployment of resource-constrained sensors, prioritizing the development of lightweight and feasible communication protocols. This approach often relegated security to an afterthought, leaving vulnerabilities unaddressed in protocols widely adopted across the industrial sector.
As we move towards fully realizing the industry 4.0 vision, addressing these security concerns becomes paramount, not only to protect sensitive data but also to ensure the integrity and resilience of the industrial processes that our increasingly interconnected world depends on.
Security in IIoT Communication Protocols
Most of the IIoT applications needs a dense mesh of sensors, often computationally and energy-constrained in nature, which collects data. Those are data feeding machine learning algorithms, which in their turn refine decision-making processes and aim at augmentation and smartization of manufacturing. Resource constraints of the devices meant that the IIoT development trajectory has historically been security-light and skewed towards the optimization of communication protocols.
In the present IIoT scenario, the dominant industrial communication protocols (MQTT, AMQP, and XMPP) base their security models on best practices at the transport layer, subscribing to either Transport Layer Security (TLS) or Datagram Transport Layer Security (DTLS) in their modeling of the secure versions.
Table 1: Comparison between TLS and DTLS
| Feature | TLS | DTLS |
| Protocol | Uses TCP for ordered, reliable byte stream. | Uses UDP for faster, unordered, and simple messages. |
| Records | Segments data into transparent blocks. | Sends records needing application management. |
| Decryption | Requires sequence integrity; blocks can’t be decrypted independently. | Allows independent decryption with explicit numbers. |
| Termination | Ends with an alert signal for clean shutdown. | Transmission can end abruptly without warning. |
| Spoofing Defense | TCP handshake mitigates IP spoofing. | Uses cookies to prevent spoofing without a connection. |
TLS operates above the TCP layer and below the application layer, securing transport connections between applications like web servers and browsers. It establishes connections through algorithm agreement, secret sharing, and authentication, using symmetric encryption and data integrity for application data transfer. Sessions are initiated via a handshake protocol, with versions including TLS 1.0, 1.1, 1.2, and 1.3.
Datagram Transport Layer Security (DTLS), detailed in RFC 6347 (V1.2), is a session layer protocol ensuring data privacy. Designed for low-latency, authenticated, and encrypted data delivery, DTLS uses the User Datagram Protocol, aiding time-sensitive communications like VoIP, DNS lookups, and media playback. DTLS prevents data loss and order errors through a retransmission timer, with endpoints continuously retransmitting the last message until a reply is received.
While important as a basis for secure communication, however, these increasingly appear, in the emerging consensus of the field, to be insufficient. It is at the level where IIoT is no longer regarded as a young offshoot of industrial communication; it turns out to be the lifeblood of modern production and process optimization.
There is a growing recognition that while establishing secure transport channels is a step in the right direction, it is only a piece of the security puzzle. The IIoT necessitates a robust framework that extends beyond transport layer security, incorporating application layer security mechanisms tailored for the unique challenges of IoT environments.
The traditional internet is replete with such mechanisms, refined over years of development and widely implemented. However, these conventional security solutions, designed for resource-rich devices, clash with the limited computational and storage capacities characteristic of most IIoT devices.
Emerging Security Risks in Industry 4.0
Industry 4.0 is defined by its ambitious goal to revolutionize the manufacturing landscape through digitization, automation, and data integration. At its heart lies the interconnection of machines, workpieces, and systems across the entire production chain.
As it stands, Industry 4.0’s reliance on massive data aggregation and advanced artificial intelligence (AI) for decision-making offers unprecedented improvements in efficiency and productivity. Nevertheless, this evolution is not without its drawbacks; it inadvertently creates a breeding ground for sophisticated security vulnerabilities, previously unknown to industrial systems that once operated in relative isolation.
The security challenge in Industry 4.0 stems from its foundation on a dual-nature core—a blend of operational technology (OT) and information technology (IT). This fusion introduces IT-centric threats into the traditionally safer OT domain, exposing it to a full spectrum of internet-borne risks. IT systems face well-documented threats ranging from malware to ransomware, which, when intersecting with critical industrial control systems (ICS), significantly raise the stakes, potentially leading to data breaches or catastrophic failures.
IIoT devices, often resource-constrained, lack robust security features found in more capable IT hardware. These devices are increasingly active decision points, processing and transmitting sensitive operational data, thus broadening the attack surface for exploitation by malicious actors.
While TLS and DTLS offer crucial encrypted communication channels, they form just the outer layers of the complex, multi-tiered security architecture required by Industry 4.0. Beyond secure transport layers, there is a critical need for defense-in-depth strategies that address security at the application layer, protecting data at rest, in use, and in motion.
Given the distributed and vulnerable nature of IIoT devices, Industry 4.0’s security approach must be holistic, pervasive, and anticipatory, capable of adapting to new threats. This new security frontier demands an architecture that not only counters known threats but is also flexible enough to adapt to emerging risks, ensuring operational continuity and integrity as the convergence of OT and IT becomes more pronounced and inherently more vulnerable.
Advanced Application Layer Security
In the arena of Industry 4.0, where the sophistication of cyber threats continues to escalate, the need for advancing security beyond the foundational transport layer is pressing. IIoT devices, typically constrained by their computational resources, necessitate security mechanisms that are not just robust, but also resource-efficient. This delicate balance between security and feasibility is where the challenge of enhancing application layer security in IIoT lies.
Object Security for Constrained RESTful Environments (OSCORE) has emerged as a proposed solution for application layer security, offering data confidentiality and integrity for CoAP (Constrained Application Protocol) messages. While OSCORE represents a significant step in the right direction, its specificity to CoAP limits its applicability across the diverse protocols employed in IIoT.
Furthermore, as IIoT ecosystems evolve to incorporate smart sensors and actuators capable of acting as independent servers, the model of security needs to be re-envisioned. Unlike traditional IoT setups that typically involve sensors transmitting data to a central server, next-generation IIoT envisions direct end-to-end (E2E) connections. This shift demands robust access control measures to ensure that only authorized entities can interact with these intelligent devices, modifying configurations and retrieving data.
This E2E approach introduces the requirement for security mechanisms that can discern not only the permissions but also the contextual conditions—like battery level or environmental factors—impacting device operation. As such, access control solutions for IIoT must be expressively designed to evaluate a wide range of parameters, ensuring flexible yet secure access management.
Although strides have been made to adapt traditional access control models for IIoT, the unique resource constraints of IIoT devices often render these adaptations impractical. Centralized control models that fail to consider local device context fall short in dynamic industrial settings, where conditions change rapidly and frequently.
The solutions must not only be light on resources but also encompassing in their protection, ensuring the integrity of both data and the devices that process it. This dual focus on efficiency and security will underpin the next wave of innovation in application layer security for IIoT, supporting the safe and seamless operation of smart manufacturing processes that are the hallmark of Industry 4.0.
Hardware-Intrinsic Multi-Layer Security
Addressing security vulnerabilities intrinsic to IIoT applications requires a fundamental shift in the perception and implementation of security mechanisms, motivating the integration of hardware-intrinsic multi-layer security measures.
Physically Unclonable Functions (PUFs) are poised to become a cornerstone in the realm of hardware security, particularly within FPGA-based IIoT devices. PUFs leverage the unique physical variations of hardware during the manufacturing process to generate secure cryptographic keys. When embedded within a multi-layer cloud computing model, PUFs serve as a secure root of trust that’s impervious to cloning or spoofing, thus significantly enhancing the defense against direct physical attacks.
The Multi-Layer Security Model
The multi-layer security architecture proposed by Al-Aqrabi, H et al. weaves together FPGA-based PUF hardware with the National Institute of Standards and Technology (NIST) cloud model, creating a robust security mesh. This hybrid model is specifically tailored to manage the high volume of device authentication requests inherent in 5G-enabled IIoT environments.
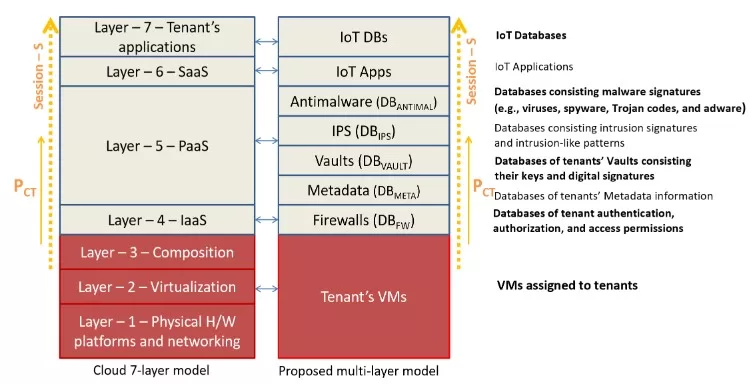
Figure 1 Multi-layer security model proposed by Hussain Al-Aqrabiet al.(dx.doi.org/10.3390/s20071963)
In the diagram, each layer represents a tier in the cloud computing model, and each tier is reinforced with a PUF. As requests flow through the model, they’re authenticated at each layer by the associated PUF, ensuring only verified traffic proceeds. This process, underpinned by the elastic nature of cloud computing and the inherent security features of PUFs, allows for rapid and secure authentication in under a second, even under heavy load.
Building on the previously discussed advanced application layer security, the implementation of hardware-intrinsic multi-layer security provides a comprehensive, hardware-rooted defensive strategy for 5G-enabled IIoT ecosystems. The unique combination of hardware resilience in PUFs and the flexibility of cloud-based security models paves the way for creating an impregnable shield against the multifaceted threats targeting IIoT.
Conclusion
In summary, the integration of 5G technology into the IIoT enables transformative benefits such as enhanced data transmission speeds, reduced latency, and increased reliability. These advancements are crucial for meeting the demands of modern industrial applications and realizing the potential of Industry 4.0. However, this technological evolution brings with it significant security challenges that must be addressed to protect sensitive data and ensure the integrity of automated industrial processes.
Furthermore, it is imperative that security strategies evolve beyond traditional models to include robust, multi-layered frameworks that address both transport and application-layer vulnerabilities. As IIoT continues to expand, embracing comprehensive and adaptive security measures will be crucial for safeguarding against the sophisticated threats inherent in these highly interconnected environments. This proactive approach will ensure the continued efficacy and safety of IIoT systems within the broader landscape of Industry 4.0.
Reference
- Al-Aqrabi, H., Johnson, A.P., Hill, R., Lane, P., Alsboui, T., “Hardware-Intrinsic Multi-Layer Security: A New Frontier for 5G Enabled IIoT,” Sensors, vol. 20, no. 1963, 2020.
- Herder, C., Yu, M.-D., Koushanfar, F., & Devadas, S. “Physical Unclonable Functions and Applications: A Tutorial,” Proceedings of the IEEE, vol. 102, no. 8, pp. 1126–1141, Aug. 2014.
- Trimberger, S., & Moore, J. “FPGA Security: Motivations, Features, and Applications,” Proceedings of the IEEE, vol. 102, no. 8, pp. 1248–1265, Aug. 2014.
- Roman, R., Zhou, J., & Lopez, J. “On the features and challenges of security and privacy in distributed internet of things,” Computer Networks, vol. 57, no. 10, pp. 2266–2279, 2013.

