Introduction
In the dynamic landscape of the Fourth Industrial Revolution, or Industry 4.0, the role of the Industrial Internet of Things (IIoT) is expanding with unprecedented momentum. The fusion of sophisticated automation, data exchange, and advanced manufacturing techniques has instigated a paradigm shift, spotlighting the need for more intricate, secure, and efficient communication protocols.
While established communication protocols have laid a foundational framework for IIoT integration, the evolving needs of Industry 4.0 demand advancements that address the contemporary challenges of security, data integrity, speed, and interoperability.
This article presents a detailed breakdown of IIoT connectivity protocols, mirroring the OSI model but tailored for IIoT scenarios. This comprehensive list includes IEEE standards and significance of each protocol, from ensuring precise timing and prioritizing critical data frames to path reservation and network redundancy.
This article is based on the innovations heralded by the likes of 3GPP Release 17 and anticipated features of Release 18. A detailed overview of key TSN standards further underscores their roles in ensuring efficient IIoT operations.
Evolution of IIoT Communication Protocols
The journey of IIoT communication protocols is marked by continuous innovation and adaptation to meet the increasing demands of industrial automation, data volume, and operational complexity.
Picture a world where wired connections were the norm, and each protocol was an island, designed for specific tasks but isolated. It was a time of simplicity but also of limitations. The flexibility was minimal, scalability a challenge, and the word ‘interoperability’ hadn’t quite found its place in the lexicon of industrial communication.
Embrace of Internet Protocols
Enter the era of Internet Protocols – a time that marked the fusion of the operational and informational worlds. 6LoWPAN stood at the forefront, a bridge that connected resource-constrained devices with the boundless world of IP connectivity. It was more than a technological leap; it was a cultural shift, heralding an age of global accessibility and unprecedented interoperability.
The Security Awakening
As we waded deeper into the waters of complexity and connectivity, the silent spectres of security and data integrity loomed large. Protocols like WirelessHART and ISA100 rose to the occasion, weaving in layers of security, encryption, and reliability that would stand as sentinels in the dynamic world of industrial communication.
Peering into the Future
So, what’s next on the horizon? We’re on the cusp of a future where AI and machine learning are not just buzzwords but integral components of IIoT communication protocols. Release 18 is not just another update; it’s a gateway to a world where challenges specific to various IIoT sectors are addressed with precision and innovation.
IIoT Connectivity Protocols
These aren’t just lines of code or technical specifications; they’re the silent conductors of the grand symphony of Industrial Internet of Things. Each has its own melody, rhythm, and harmony – creating a mosaic of connectivity that defines our modern industrial landscape.
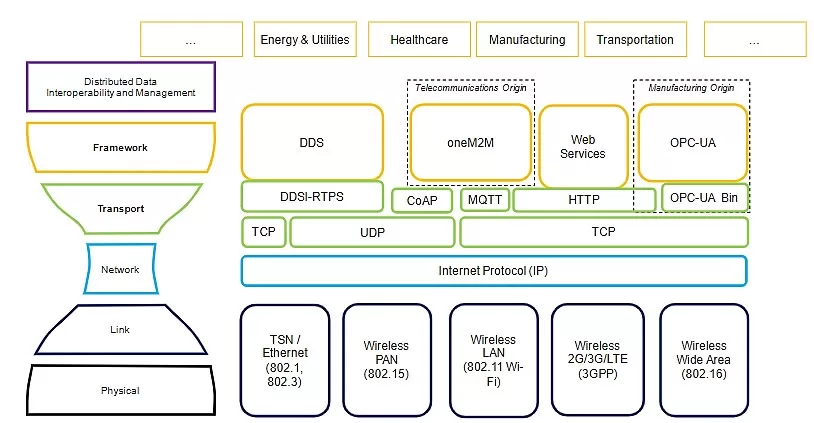
Figure 1: IIoT Connectivity Protocols Stack
This hierarchical representation resembles the OSI model but is adapted for IIoT contexts. Let’s break down each layer and the associated protocols:
Physical Layer
This is the foundational layer where the actual transmission and reception of raw data bits occur across a physical medium. The protocols and technologies listed in this layer involve different ways in which data is physically sent and received over networks.
Protocols and Technologies:
- TSN/Ethernet (802.1, 802.3): Time-Sensitive Networking (TSN) is a set of standards under the IEEE 802.1 umbrella. TSN allows for real-time communication over Ethernet networks. IEEE 802.3 is the standard for the Ethernet itself, which is a technology that facilitates data transfer in local area networks (LANs).
- Wireless PAN (802.15): This refers to Wireless Personal Area Networks. The IEEE 802.15 standard covers this category, which includes technologies designed for short-range personal or device-to-device communications. With its low-rate wireless personal area networks, this protocol is the embodiment of reliability, yet it whispers the modesty of low-cost communication.
- Wireless LAN (802.11 Wi-Fi): This is the protocol for Wireless Local Area Networks, commonly known as Wi-Fi. It facilitates medium-range wireless communication, typically used for internet connectivity in homes, offices, and public spaces.
- Wireless 2G/3G/LTE (3GPP): This covers the cellular communication protocols standardized by 3GPP. These technologies (2G, 3G, LTE) represent different generations of cellular technology, with LTE being a precursor to the modern 4G.
- Wireless Wide Area (802.16): This is commonly known as WiMAX, which stands for Worldwide Interoperability for Microwave Access. It’s a broadband wireless technology designed for wide-area coverage.
- 6LoWPAN: 6LoWPAN is akin to a bridge that links the quaint town of low-power, wireless personal networks to the bustling city of Internet Protocol (IPv6). It’s not just about connecting two points; it’s about opening a world where the ‘limited’ shakes hands with the ‘limitless’.
- Z-Wave: With Z-Wave, think of a home where appliances converse, lights, locks, and thermostats dance to the tunes of wireless commands. It’s not just home automation; it’s about weaving the fabric of a living space that breathes and responds, adapting to the needs of its occupants.
- ISA 100: Industrial automation finds a reliable companion in ISA 100. It’s security wrapped in efficiency, offering a double layer of protection while ensuring the seamless integration with wired networks. It’s as much about safeguarding communication as it is about enhancing it.
- Bluetooth: Then there’s Bluetooth, an old friend in a new world. In the realm of IIoT, it metamorphoses into a swift, efficient channel that binds devices in an invisible thread of communication, echoing the simplicity of connection and the speed of data transfer.
- NFC: NFC is like that silent whisper that communicates volumes. With just a touch or a close proximity, it enables devices to exchange data, making it a favorite in applications where simplicity and speed are of the essence.
- RFID: RFID stands as a silent guardian of identification and tracking. In the world where every piece of data, every product, and asset is a drop in the ocean of IIoT, RFID is the lighthouse that ensures nothing is lost, and everything is accounted for, efficiently and securely.*
Link Layer
This layer is responsible for establishing a reliable link between two directly connected nodes. It facilitates the error-free transfer of frames between these nodes and controls the flow of data.
Network Layer
This layer is designated by the Internet Protocol (IP), a protocol used for transmitting data across a packet-switched network. IP handles addressing and routing of packets so that data can travel across networks and arrive at the correct destination.
Transport Layer
The transport layer provides end-to-end communication services for applications. It ensures the complete and error-free transmission of data.
Protocols:
- TCP: The Transmission Control Protocol is a connection-oriented protocol that ensures reliable, ordered, and error-free delivery of data.
- UDP: The User Datagram Protocol is a simpler, connectionless protocol. It is faster and requires fewer resources than TCP but doesn’t guarantee the delivery of packets.
Framework Layer
This layer deals with frameworks that provide robustness to IIoT applications by offering services like data management, security, and device management.
Protocols and Technologies:
- DDS: Data Distribution Service for real-time systems. It provides high-performance data connectivity for IIoT applications.
- oneM2M: A global standard for M2M and IoT technologies. It provides a framework for device and service management.
- Web Services: These are standard methods of interoperating between software applications running on a variety of platforms and frameworks.
- OPC-UA: Open Platform Communications Unified Architecture is a machine-to-machine communication protocol for industrial automation.
It’s also worth noting the image separates frameworks based on their origins – some are from a telecommunications perspective (e.g., oneM2M), while others stem from manufacturing (e.g., OPC-UA).
Lastly, the top layer indicates different industries that utilize these protocols, such as Energy & Utilities, Healthcare, Manufacturing, and Transportation.
Time Sensitive Communications Enablers
The integration of 5G into the Industrial Internet of Things (IIoT) environment is a pivotal advancement heralded by the 3GPP Rel-16, and Rel-17, which aspires to seamlessly incorporate the capabilities of 5G New Radio (NR) into Industrial Ethernet settings utilizing IEEE time-sensitive networks (TSN).
TSN, a layer-2 solution, is instrumental in enhancing the determinism of Industrial Ethernet by offering features such as network-wide scheduling, meticulous traffic reservation, shaping, pre-emption mechanisms, and redundancy methods. An integral component of this progression is the common time synchronization achieved through IEEE802.1AS, ensuring synchronized operations across networking components and devices.
The imperative behind Time-Sensitive Communications (TSC) is to facilitate both deterministic transport and the absolute time synchronization of devices, which are quintessential for TSN. The TSC approach builds heavily upon the URLLC and eURLLC solutions, aiming to guarantee short and assured packet delays.
Building on our discussion of Time-Sensitive Networking (TSN) in IIoT, it’s crucial to understand the specific standards that constitute this network. The following table offers an insightful breakdown of these standards:
Table 1: Breakdown of TSN Protocol standards
| STANDARD | DESCRIPTION |
| IEEE 802.1ASrev & IEEE 1588 | Timing & Synchronization |
| IEEE 802.1Qbu & IEEE 802.3br | Frame Preemption |
| IEEE 802.1 Qbv | Enhancements for Scheduled Traffic |
| IEEE 802.1 Qca | Path Control & Reservation |
| IEEE 802.1 Qcc | System Configuration |
| IEEE 802.1Qci | Per-Stream Filtering & Policing |
| IEEE 802.1 CB | Seamless Redundancy |
- IEEE 802.1ASrev & IEEE 1588: These standards primarily deal with “Timing & Synchronization” within the network. Ensuring precise timing across devices is paramount for many IIoT applications where even a slight offset can lead to significant disruptions.
- IEEE 802.1Qbu & IEEE 802.3br: They address “Frame Preemption.” This is about ensuring that critical data frames are given precedence and can preempt other non-critical frames, ensuring timely delivery.
- IEEE 802.1 Qbv: This is concerned with “Enhancements for Scheduled Traffic.” It allows for the scheduling of data traffic, ensuring that high-priority tasks are assigned the necessary bandwidth at the right time.
- IEEE 802.1 Qca: Under the purview of “Path Control & Reservation,” this standard outlines how paths are established and reserved within the network, which is crucial for ensuring data gets to where it needs to go without delay.
- IEEE 802.1 Qcc: This touches on “System Configuration,” a crucial aspect ensuring that the entire system is correctly set up to handle the specific demands of IIoT applications.
- IEEE 802.1Qci: This delves into “Per-Stream Filtering & Policing,” ensuring that individual data streams are correctly filtered and managed, ensuring network integrity and efficiency.
- IEEE 802.1 CB: A cornerstone of any network, this standard addresses “Seamless Redundancy.” This ensures that in the event of a system failure or another disruption, there are backup paths and mechanisms in place to keep data flowing without interruption.
Conclusion
The evolution of IIoT communication protocols signifies the merging of traditional industrial systems with advanced technologies, paving the way for a more interconnected and secure future. As we integrate AI and 5G into the IIoT landscape, it’s evident that the focus is shifting towards achieving seamless, efficient, and secure communication. The outlined standards and protocols act as the backbone of this transformation, ensuring that as the IIoT ecosystem grows, it remains robust, adaptable, and future-ready.
References
- 3GPP ETSI TS 23.501. System Architecture for the 5G System (5GS). V16.6.0, 2020-10.
- Nurul Huda Mahmood, Nikolaj Marchenko, Mikael Gidlund, Petar Popovski, “Wireless Networks and Industrial IoT”, Springer, https://doi.org/10.1007/978-3-030-51473-0
- Lauridsen, I. Z. Kovacs, P. Mogensen, M. Sorensen and S. Holst, “Coverage and Capacity Analysis of LTE-M and NB-IoT in a Rural Area,” 2016 IEEE 84th Vehicular Technology Conference (VTC-Fall), Montreal, QC, 2016