Introduction
The Internet of Things (IoT) promises to bring everything from microwaves to pacemakers and shipping fleets online, leverage enormous amounts of new data, and ultimately, make our world smarter, easier, and more efficient.
When it comes to the Internet of Things (IoT), the security challenges and the support involved couldn’t be more significant. The spread of IoT in homes, enterprises, industries, governments, and other places is making wireless networks the backbone of the country’s critical infrastructure. Safeguarding it against potential threats is a basic need.
IoT security indeed is very complex and multifaceted. The entire system, including the infrastructure, devices, and the links that connect them, need to be secured to be effective.
Reports have shown that IoT market size in Europe is estimated to reach €242,222 million by the end of 2020, with forecasts also predicting that this form of technology (IoT and end-user solutions) in the global market, will grow to an estimated $1.6 trillion by 2025.
Why Security is challenge number 1 in IoT?
IoT devices, to be useful, they must make realtime bi-directional connections to the internet, and that type of communication is challenging to secure. Whereas security protocols and best practices for servers, personal computers, and smartphones are well-understood and broadly adopted, security for IoT devices is nascent and rarely sufficient.
IoT modules, being at the heart of IoT devices, are fundamental to the system security. Unlike smartphones, modules are simple and very vulnerable to intrusion. Any compromised module exposes the entire system and puts it at risk. Hence module security must be complete, including the device hardware, software, firmware, and management system that facilitate ongoing operational security throughout the device lifecycle.
The responsibility of securing the IoT modules typically falls on the shoulders of module vendors, as many IoT device vendors and users may not have the expertise or the means to access and secure the module themselves.
The Biggest security challenges for IoT
- Insufficient testing and updating, Most of these devices and IoT products don’t get enough updates while some don’t get updates at all. This means that a device that was once thought of as secure when the customers first bought it becomes insecure and eventually prone to hackers and other security issues.
-
Brute-forcing and the issue of default passwords, Weak credentials, and login details leave nearly all IoT devices vulnerable to password hacking and brute-forcing in particular.
-
Data security and privacy concerns, Data is constantly being harnessed, transmitted, stored, and processed by large companies using a wide array of IoT devices, such as smart TVs, speakers, and lighting systems, connected printers, HVAC systems, and smart thermostats. If the data is stored, then the largest challenge is in compliance with various legal and regulatory structures.
- AI tools and automation risks in IoT, The massive amount of user data can be quite difficult to manage from a data collection and networking perspective. AI tools and automation are currently being utilized to filter through large amounts of data and could help IoT administrators and network security officers enforce data-specific rules and detect anomalous data and traffic patterns. However, using autonomous systems to make autonomous decisions that affect millions of functions across large infrastructures such as healthcare, power and transportation might be too risky, especially once you consider that it only takes a single error in the code or a misbehaving algorithm to bring down the whole infrastructure.
What Is End-to-End IoT System Security?
Cellular IoT is a complex system, and its security is equally complex. For it to be effective, one must address the full system. The system typically consists of many parts, but from the security point of view, mainly three logical parts:
1. The IoT device with all its software, firmware, hardware, applications, etc.
2. The cellular network infrastructure, including the radio network, the core network, etc.
3. The cloud that connects the IoT network to the outside world, which could include the user cloud that houses the IoT user applications, connection to many kinds of systems that use the IoT network as well as the cloud platform for managing the IoT devices.

An end-to-end approach is a must for overall IoT system security
IoT Modules Are Key to IoT Device Security
The module is the brain of the cellular IoT device. Module vendors take barebones chipsets from vendors like Qualcomm and Intel and add their software and additional hardware to create modules with standard interfaces. Device manufacturers develop their machines based on these modules.
Modules simplify the connectivity and operator certification-related complexity, so device vendors concentrate on developing use-case-specific devices. So, the responsibility of IoT device security rests on the shoulders of module vendors.
Due to device vulnerability, the integrity of the supply chain of IoT devices and especially modules is key not only for system security but also for national security. IoT users should know where the vendor manufactures the modules and what safety measures they have in place to ensure the manufacturing process does not compromise the device and module integrity at any stage.
4 Steps for Securely Provisioning IoT Devices
Devices connected to a secure IoT network should make only outbound connections as in a traditional model, the listening device will open an inbound port and wait for data to be pushed. While this can work in some scenarios, it is a massive risk for IoT as these ports must remain open indefinitely. These connections are not vulnerable to the kind of attacks that open inbound ports are.
So The outbound-only design pattern eliminates one major threat to IoT devices. To support this design pattern, we’ll also need to use
a publish/subscribe communication design so devices can send data bi-directionally.
- A new device subscribes to the Announce channel, A publish/subscribe paradigm that uses the standard outbound ports 80 and 443 make it easy to securely set up and provision IoT devices. When it’s plugged in, the device wakes up, subscribes to a designated Announce channel, and announces itself to the data stream network.
- The server returns the private channels, The server then returns a private channel on which the device and server can communicate. The server can then set access rules on the channel and provisions from there. All of this happens immediately, giving the consumer the plug and play experience she expects.
- Device subscribes to private channels with secret.
- The server checks secret & decides to provision.
E2E IoT security architecture
The purpose of an E2E IoT security architecture is to ensure the security and privacy of IoT services, protect the IoT system itself and prevent IoT devices from becoming a source of attacks – a Distributed Denial of Service (DDoS) attack, for example – against other systems.
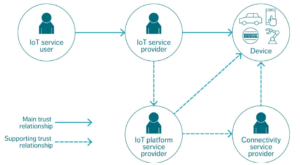
The main and supporting IoT actors and their trust relationships
The three main actors in an IoT solution are the IoT service user, the IoT service provider, and the devices that enable the provision of the IoT service. The supporting actors are the IoT platform service provider, whose role is to provide the IoT platform for the IoT service provider, and the connectivity service provider, whose role is to provide connectivity for the IoT devices and service.
The trustworthiness of services and service use depends on how the actors govern identities and data, security and privacy, and the degree to which they comply with the agreed policies and regulations. The combination of security and identity functions is important for defining the trust level.
For example, hardware-based trust does not help if the application does not make use of it. A fully trusted application does not help if communication cannot be trusted.
An E2E approach is therefore essential to ensure trust among all actors across the system.
Conclusion
IoT security is very complex and multifaceted. It requires an end-to-end approach to secure the complete system, including the devices, infrastructure, cloud, all the links that connect them, all the hardware, firmware, and software. Network security is only as strong as its weakest link. Simple IoT devices that lack strong processing and storage capabilities are especially vulnerable to hacking and unauthorized intrusion.
Since they are deployed in large numbers and have a long lifespan exceeding 10–15 in many cases, compromising their security might cause significant disruption. Because many critical national infrastructures run on IoT systems, it is immensely important to secure not only their networks but also scrutinize their supply chains.
Resources
- Ericsson
- PubNub.
- TantraAnalyst
- Toshiba
- PentaSecurity